There are frequent inquiries that our readers make about the possible espionage on their own mobile phones. They ask us through the comments of our blog and through the form Ask what you want and often tell us stories related to jealousy that, founded or unfounded, lead to situations of distrust and possible espionage.

Most of the time it is about conflicting situations between couples, where the woman normally suspects that the husband or ex-husband is spying on her through something that she has installed on her phone and that allows her to read all of her private conversations.
The reality is that these programs or spyware applications exist and are available to anyone just by searching the Internet, both for Android (much more widespread) and for iPhone (requires jailbreaking). More or less sophisticated, paid or free, all have in common the ability to spy “everything” that is done on the victim’s phone, sometimes even in real time. It is always necessary that someone accepts the installation of the spyware on the victim’s phone, so the author will normally take advantage of an oversight to install it without raising suspicion.
They can save and send screenshots, texts written using the keyboard, connect the camera, record videos remotely and silently, know the instant location, etc.
They are usually undetectable, since they work in the background. They do not have an icon that identifies them and they even hide themselves from the lists of running applications. Therefore, visually we will not be able to detect them and we will have to use some specialized tool to discover it.
What do I do if I think they spy on my phone?
- Use antispyware. The first step we must take is the installation of a specialized application that will allow us to detect the majority of spyware installed. They are known as “antispyware” and one of the most developed is CM Security (Android). In addition to protection against spyware, it also provides us with other functions of security and optimization of the phone, such as full antivirus and junk file cleaning.
However, for Android there are many other specialized applications in this function. If one of them does not find anything suspicious, it is advisable to check with another one, however, we will only install one of them in order not to overload the operation of the phone. Other prestigious applications are Norton Antivirus, Malwarebytes, Kaspersky or 360 Security, although there are many more.
There are also antimalware applications for iOS, which protect us from other risks in addition to malicious programs. Its use is much more indicated if we have applied the jailbreak to the device. For example Avira Mobile Security or Lookout. - Restore to factory. If after analyzing with several specialized applications no security alert appears, we can be almost completely sure that our phone is not infected and we should not worry. However, if we have reasonable suspicions that our information “leaks”, we can choose to restore the phone to factory status. This operation will clean the memory of the device eliminating any installed application that is not original. It will also erase all files such as photos, videos, music or downloaded documents, so we must make a backup copy of those we want to keep.
- Use a specialized service or change the telephone. Unfortunately, if the author of the espionage is a real hacker and has had the victim’s phone long enough, he could have installed some malicious program that could not be detected or uninstalled with the solutions mentioned above. Only if after carrying them out we have a clear record of the fact that they are still capturing information, we should think about resorting to a specialized technical service or directly changing the terminal.
Tips
Whether we have found something suspicious installed or we simply like to prevent, we must take certain measures to ensure our protection against spyware or any other malicious program.
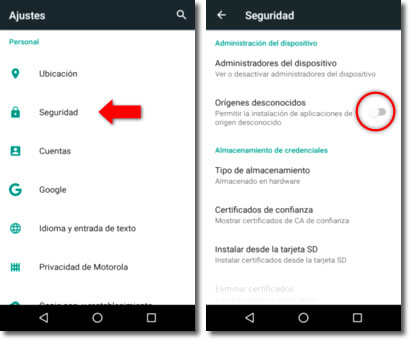
- Unknown origins. Never install applications from sources other than the official one. To do this, we only need to make sure that the phone continues with the option that allows installation from unknown sources disabled. If it remains that way, we can only install the applications supervised by Google, which in principle, provides guarantees.
- Do not neglect the telephone. To install a malicious software on an Android phone or iPhone, someone’s action on the phone itself is necessary. If we never lose sight of it in front of someone who might potentially want to spy on us, they won’t be able to install it. They may set a trap, such as sending us a message or email that proposes the installation of something, but then it will be enough to comply with the first advice, not install anything that does not come from the official store.
- Avoid obsession. Finally, it is possible that our suspicions are not so well founded and we just let ourselves be carried away by distrust. If the specialized applications do not detect anything strange and the potential spy is not an extraordinary hacker, surely our suspicion is unjustified.
